START PROACTIVE DEFENSE with EXTERNAL
Continuous Threat Exposure Management (CTEM)
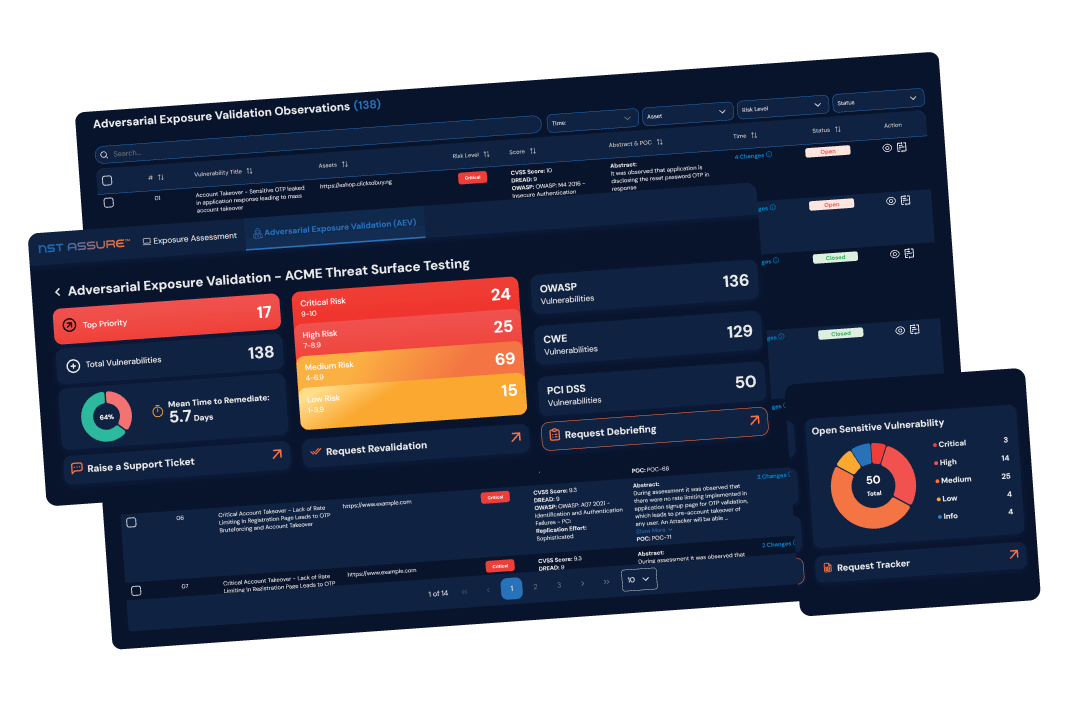
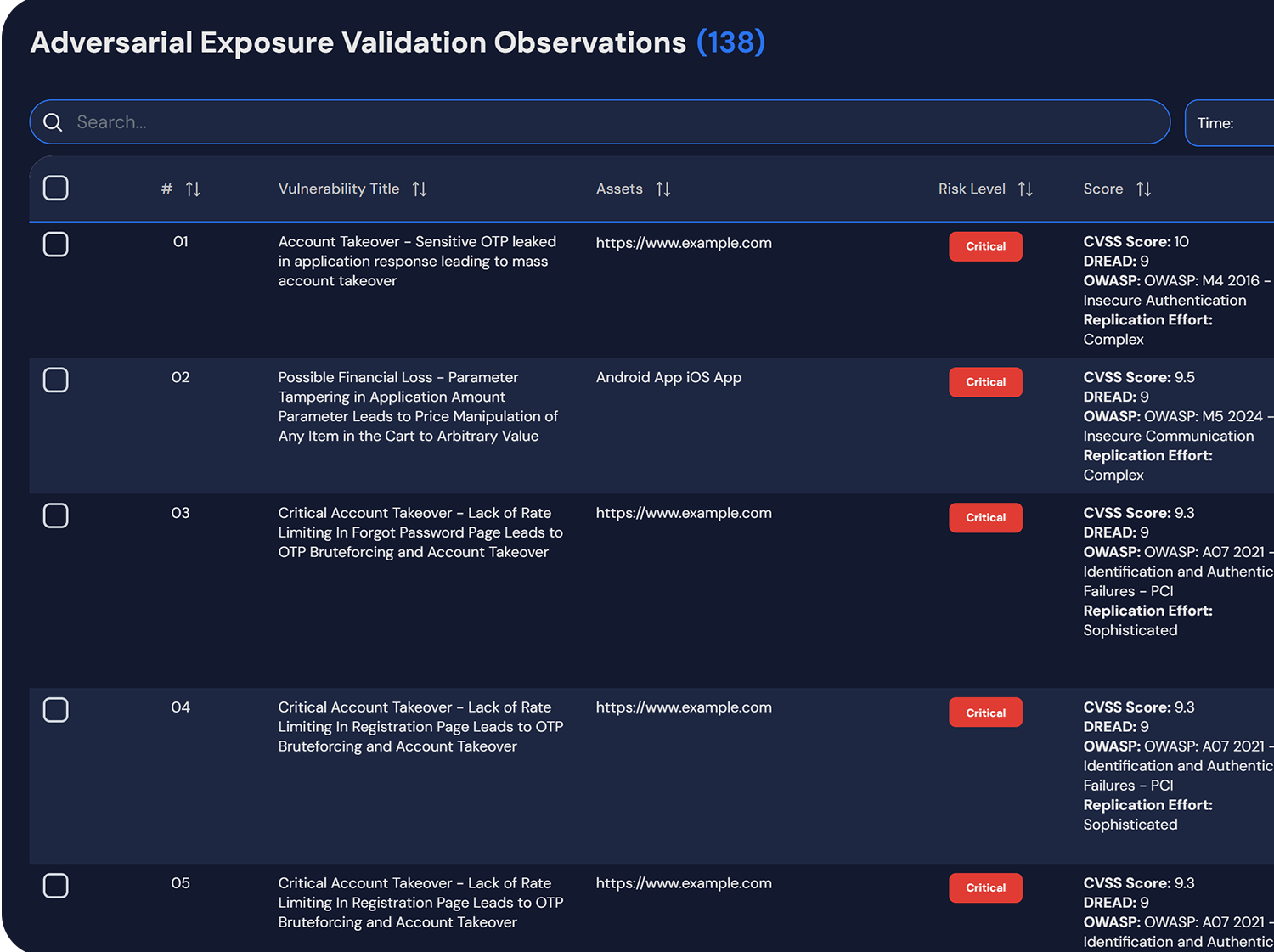
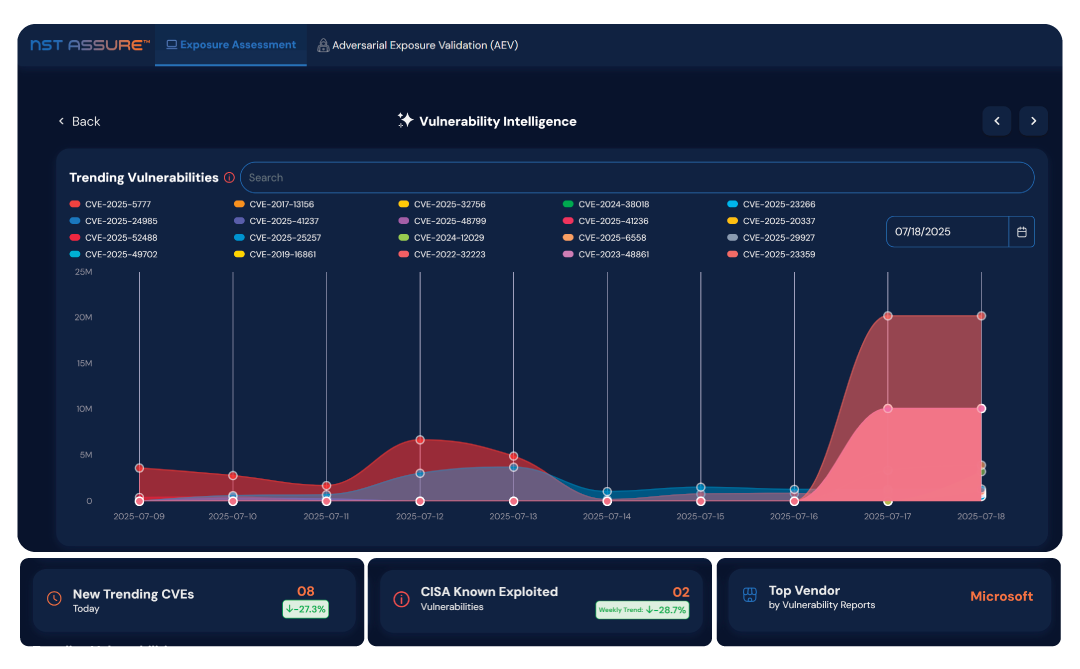
Leverage the power of NST Assure’s Exposure Assessment and Adversarial Exposure Validation (AEV) to rapidly and effectively launch external Continuous Threat Exposure Management (CTEM) programs.
By combining AI-driven analysis with expert-led adversarial validation, NST Assure empowers organizations to identify, prioritize, and mitigate high-impact exposures—transforming raw vulnerability data into actionable risk intelligence that drives meaningful and measurable risk reduction.
By combining AI-driven analysis with expert-led adversarial validation, NST Assure empowers organizations to identify, prioritize, and mitigate high-impact exposures—transforming raw vulnerability data into actionable risk intelligence that drives meaningful and measurable risk reduction.
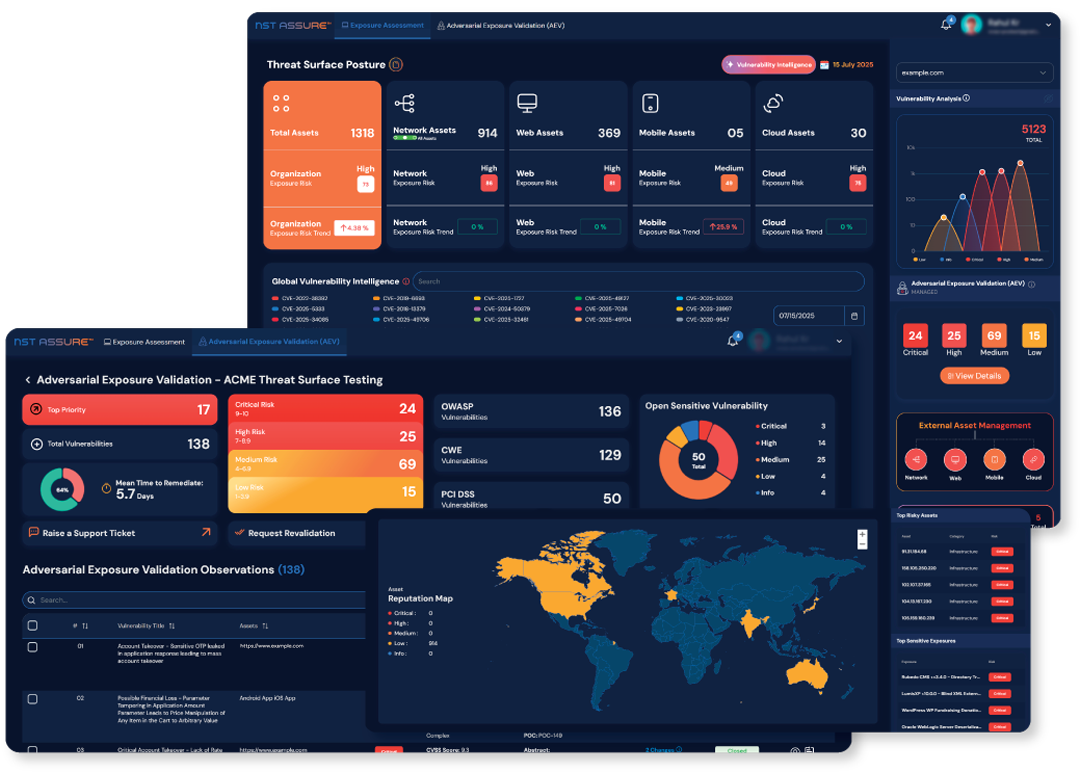
Continuous EXPOSURE ASSESMENT
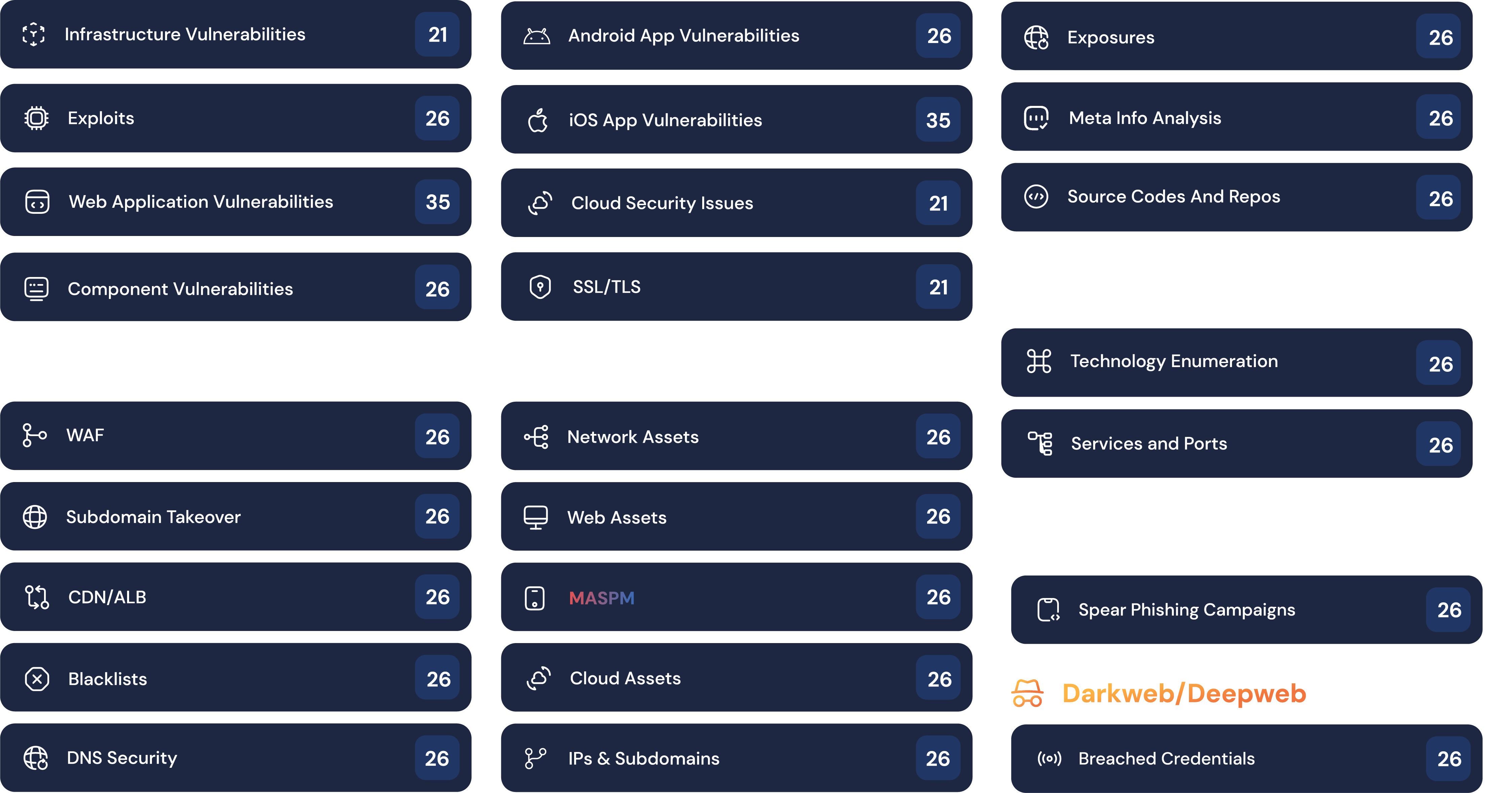
Threat Surfaces Across All Channels & Asset Types
Ensuring active Exposure Assessment and management of threat surfaces across all channels and asset types to enable comprehensive visibility, a clear understanding of the security landscape, and proactive vulnerability remediation.
01
Apps and Infra
- Web Applications
- APIs & Services
- Mobiles Apps & Cloud Apps
- Storage & Data Services
- Infrastructure Assets
All Types of Exposed Digital Assets
02
Environments
- On-Premise
- Cloud
- Hybrid
03
Channels
- Internet
- Deep Web
- Dark Web
04
Components
- Frontend/Backend Libraries
- SDKs/Plugins
- Shared Services


%201.svg)








%201.svg)











%201.svg)