Discover, Validate & Mitigate External Cyber Risks With
NST Assure’s Exposure Assessment & Adversarial Exposure Validation Platform
Safeguard your business using our Exposure Assessment and Adversarial Exposure Validation platform. Benefit from comprehensive Exposure Assessments and Adversarial Exposure Validation to drive proactive risk management, effective threat mitigation, and ensure compliance for your organization.

UNCOVER CRITICAL THREATS
AI-Powered Exposure Assessment & Adversarial Exposure Validation Platform for Proactive Security
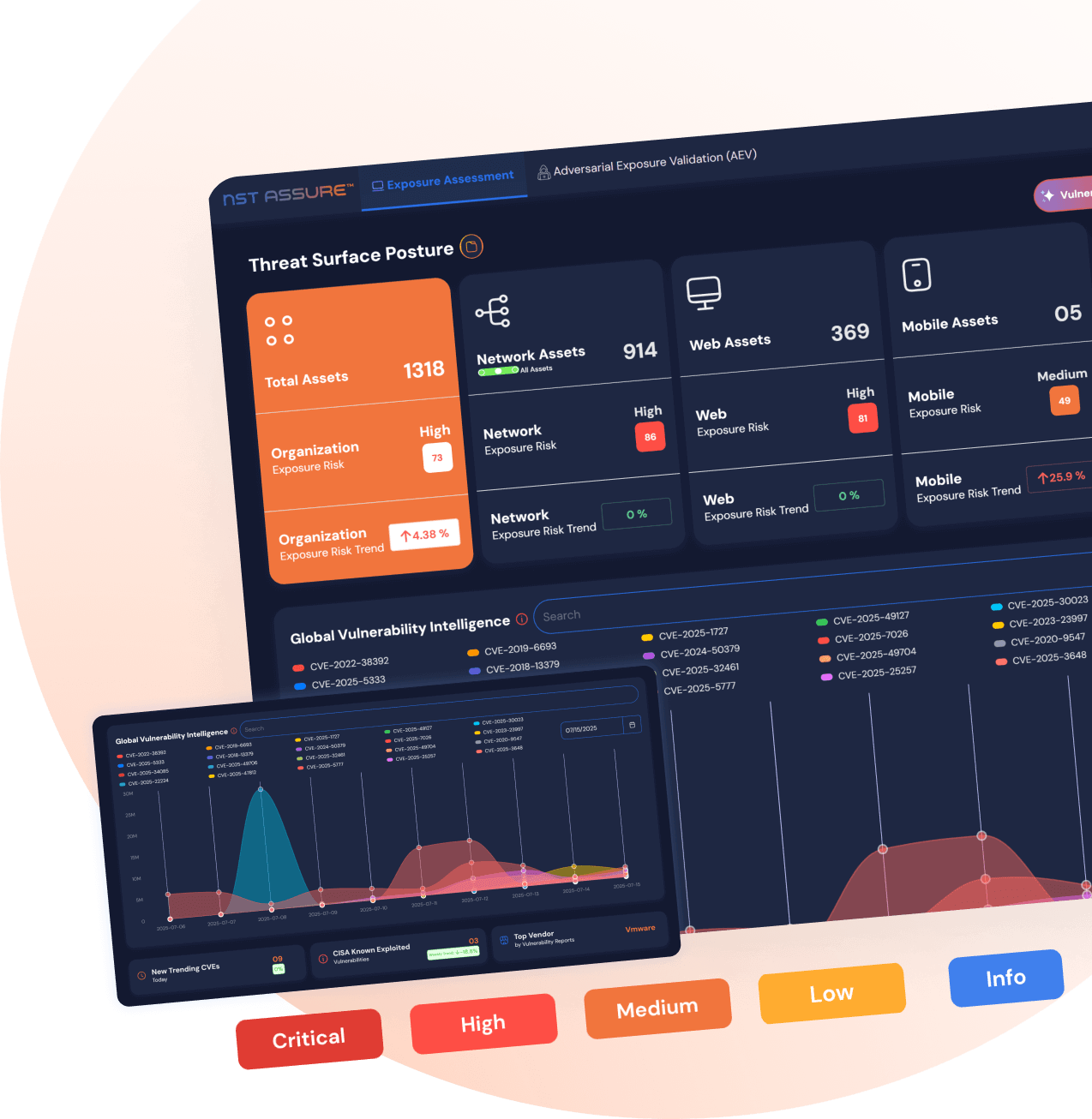
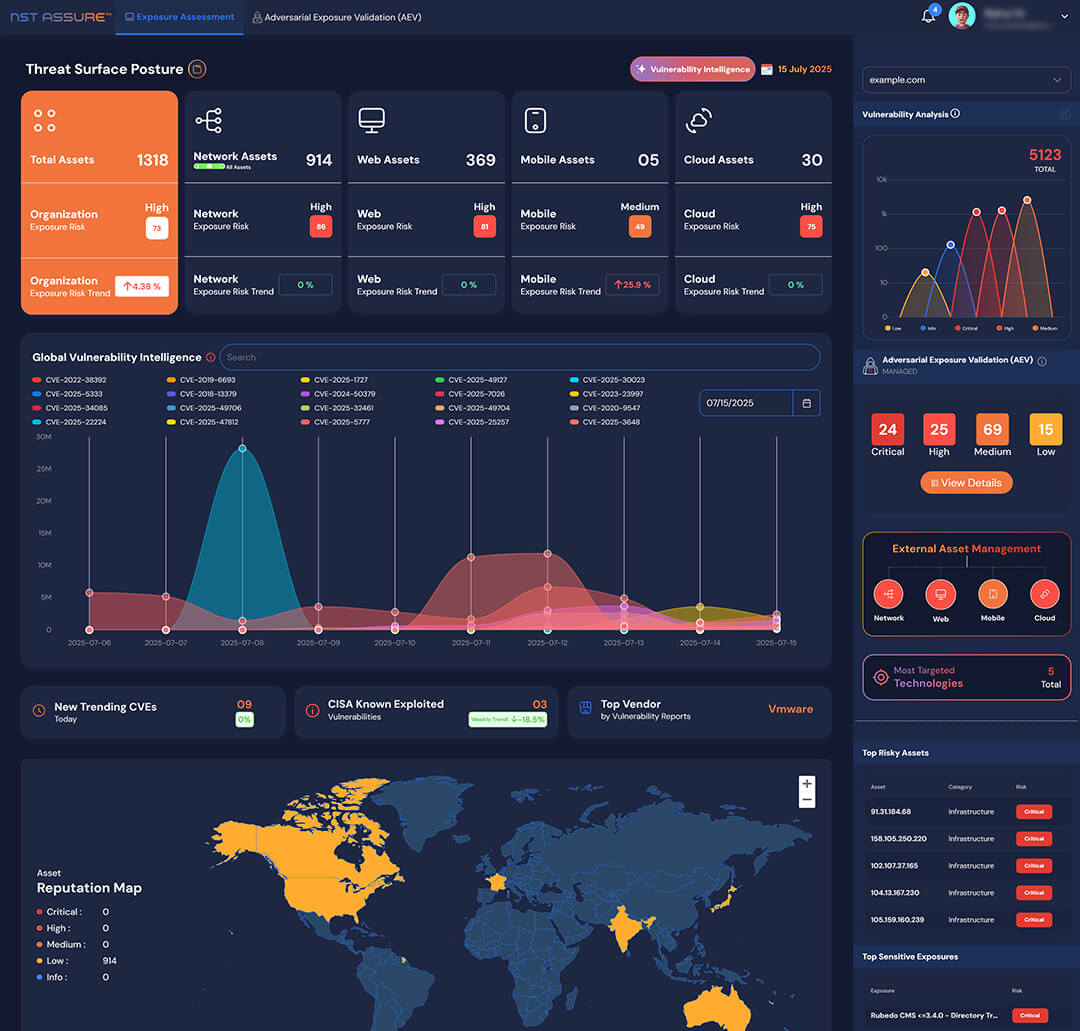
NST Assure Exposure Assessment and Adversarial Exposure Validation platform provides enterprises with a continuous, attacker-centric view of their external threat surface. By automating discovery, mapping, and contextual analysis of exposed assets and vulnerabilities, it delivers real-time visibility into potential entry points.
The platform goes beyond detection, validating exposures through safe, controlled adversarial techniques to confirm exploitability. This enables organizations to focus on what truly matters, reducing noise and prioritizing risks based on real-world impact.
NST Assure empowers security teams to proactively address validated exposures, improve operational response, and elevate overall security posture in the face of evolving threats.
The platform goes beyond detection, validating exposures through safe, controlled adversarial techniques to confirm exploitability. This enables organizations to focus on what truly matters, reducing noise and prioritizing risks based on real-world impact.
NST Assure empowers security teams to proactively address validated exposures, improve operational response, and elevate overall security posture in the face of evolving threats.
VALIDATE & RESOLVE HIDDEN RISKS
Comprehensive Exposure Assessment and Adversarial Exposure Validation with NST Assure
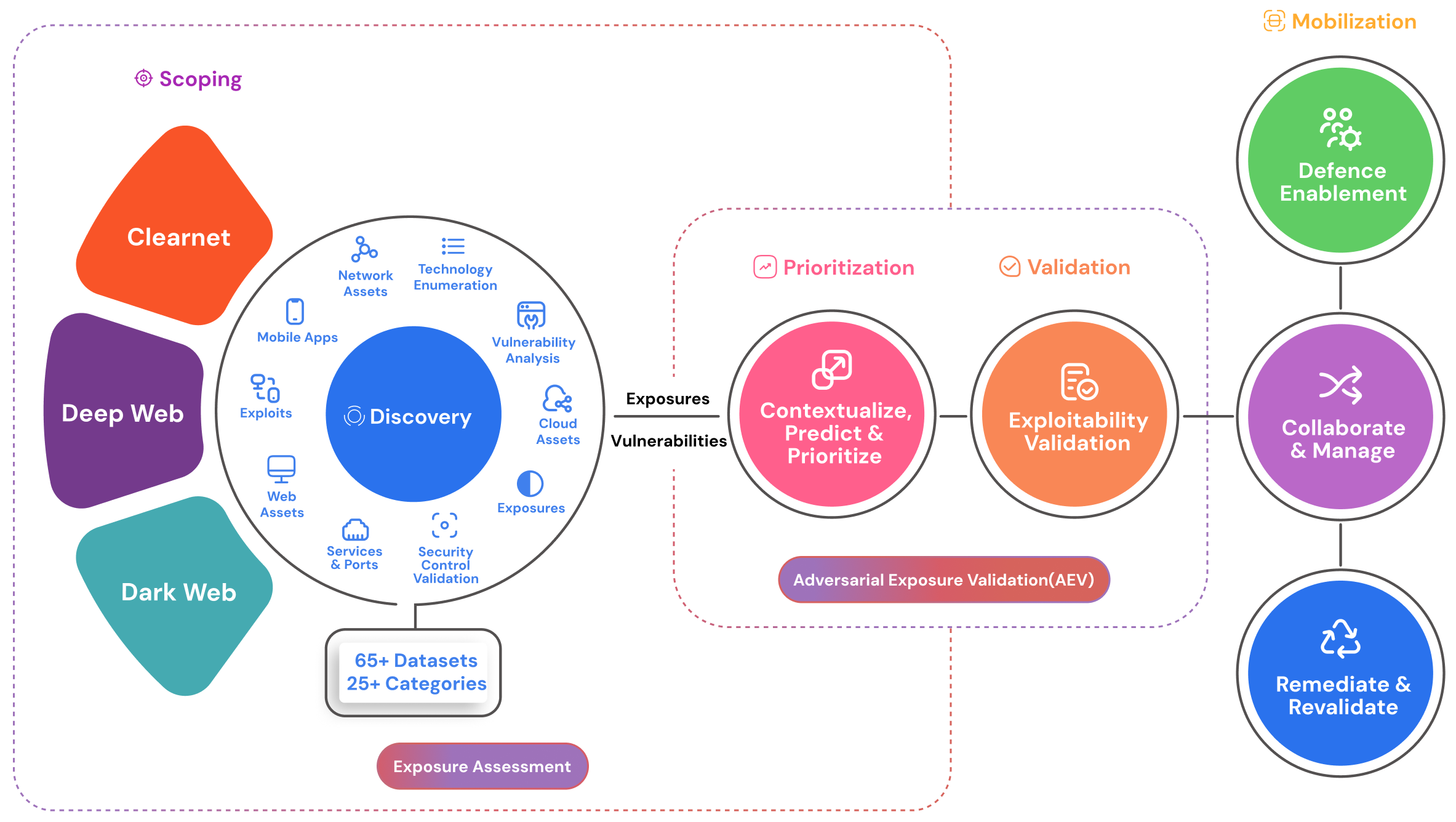
Traditional external threat management can result in vulnerability fatigue and leave risk management leaders navigating complex challenges. NST Assure streamlines adversarial exposure validation, empowering organizations to assess, prioritize, and effectively manage external risks to their digital assets. Exposure Assessment maps your attack surface; Adversarial Exposure Validation simulates real-world threats to confirm true risk and validate controls.
Evaluate Exploitation Potential
Gain clarity on the likelihood of exploitation across your attack surface, enabling focused prioritization of the most vulnerable exposures.
Catalog and Classify Exposure
Generate a detailed inventory of vulnerabilities, threat intelligence, and digital assets, creating an organized and actionable exposure profile.
Validate Defensive Resilience
Test your security controls to verify their ability to detect and prevent real-world threats, ensuring that defenses are resilient against potential breaches.
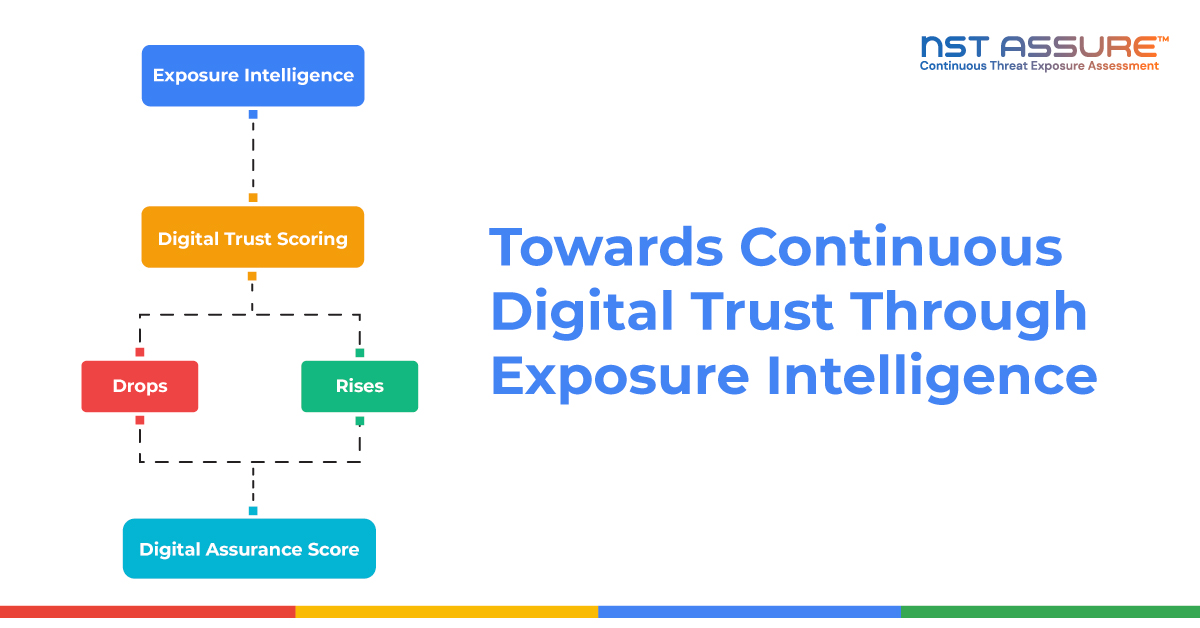
With NST Assure, organizations gain a structured approach to exposure validation, enhancing security outcomes through proactive, evidence-based risk management.
Prioritize Risk Reduction and Take Control
Gain control of your external attack surface with a proactive, intelligence-led approach. NST Assure continuously correlates Global Vulnerability Intelligence-driven by exploitation insights and trending CVEs-with your organization’s unique exposure profile to highlight high-risk vulnerabilities in real time. By focusing on adversary behavior and actual exploitability, you can prioritize risk reduction, take decisive action, and confidently protect your environment.

Continuous Monitoring
Maintain a real-time view of your exposed assets and evolving threat landscape.

Automated Assessment
Discover and assess external exposures at scale, with precision.

Threat Intelligence Correlation
Leverage NST Assure’s Global Vulnerability Intelligence to align the most exploited and trending threats with your specific environment.

Prediction & Validation
Move beyond static risk scores—predict likelihood of exploitation and validate exposures using safe adversarial techniques.

Risk Identification & Prioritization
Identify which exposures truly matter and focus remediation where it counts.
.svg)
Cyber Threat Informed Defense™ (CTID)
Build resilience based on real-world attacker behavior and validated exposure pathways.

Compliance Assurance
Meet evolving regulatory requirements with continuous visibility and audit-ready evidence.

Detection & Response Enablement
Strengthen detection strategies and accelerate incident response with validated intelligence on active exposures.
STRENGTHEN YOUR SECURITY POSTURE
Continuous Improvement Through Exploitation Intelligence and Validation-Driven Defense
NST Assure’s Exposure Assessment and Adversarial Exposure Validation platform enables precision risk reduction by focusing on what truly matters—real-world exploitability.
Exploitation Intelligence for Targeted Remediation
Move beyond surface-level vulnerability scanning. NST Assure highlights exposures actively exploited in the wild, enriched with curated intelligence to support timely and effective remediation decisions.
Adversary-Centric Asset Contextualization
Understand which of your assets align with attacker interest. NST Assure correlates adversary targeting trends with your exposed technologies, helping prioritize defense where the risk is real and contextual.

Industry and Regional Threat Focus
Leverage continuously updated intelligence on threat actors, malware, and tactics specific to your industry and region, ensuring defenses are tuned to the threats most likely to impact your environment.
NST Assure empowers organizations to elevate their external security posture through continuous, threat-informed insights.
Exposure Assessment identifies externally observable risks.
Adversarial Exposure Validation actively confirms which exposures are exploitable—prioritizing those that demand immediate attention.
Exposure Assessment identifies externally observable risks.
Adversarial Exposure Validation actively confirms which exposures are exploitable—prioritizing those that demand immediate attention.
ELIMINATE
Identity-Based Risks Before They Become Breaches
Credential exposures remain one of the most exploited attack vectors in the wild.
NST Assure continuously monitors the dark web and criminal underground to uncover compromised credentials tied to your organization before attackers can act. By aligning breach intelligence with your external attack surface, NST Assure helps you preempt credential stuffing, account takeover, and unauthorized access with unmatched precision.
NST Assure continuously monitors the dark web and criminal underground to uncover compromised credentials tied to your organization before attackers can act. By aligning breach intelligence with your external attack surface, NST Assure helps you preempt credential stuffing, account takeover, and unauthorized access with unmatched precision.
JOIN THE SECURITY REVOLUTION
Eliminate Risks that can Lead to Breaches

How does my organization look like from an attacker's perspective?
NST Assure’s Exposure Assessment and Adversarial Exposure Validation directly answer this question using real-world threat modeling and validation techniques.
NST Assure’s Exposure Assessment and Adversarial Exposure Validation directly answer this question using real-world threat modeling and validation techniques.

How well-prepared are we to defend against an attack, and how would our processes perform under stress?

What software and configurations make us vulnerable to attack?

How can I continuously & proactively eliminate the chances of a breach?
FEATURED THIS MONTH IN
Blogs
Offensive Security Consulting
Looking for top-tier offensive security services like penetration testing and red teaming ? Get in touch with NetSentries, the premier global provider of offensive security solutions for banking and enterprise.